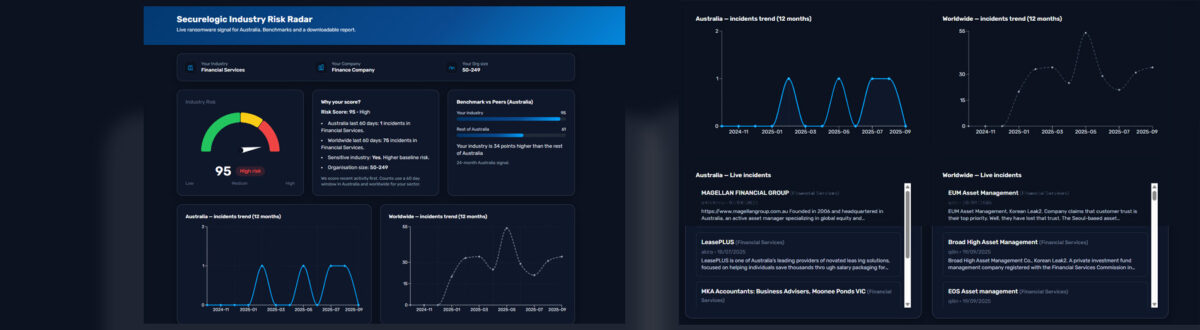
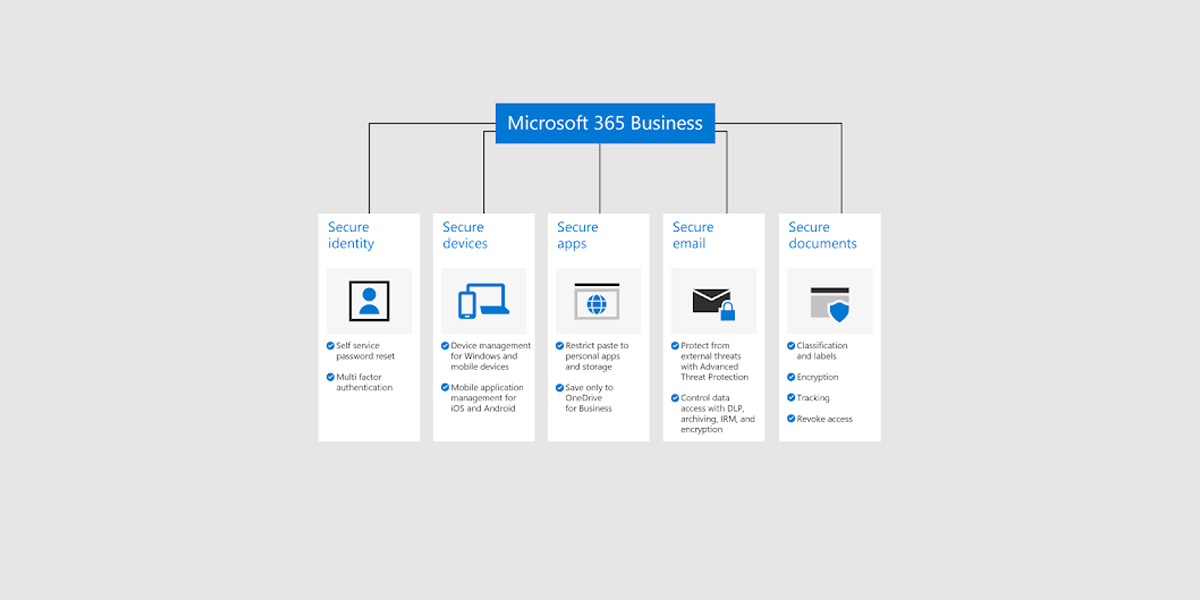
In 2022, even companies like Microsoft are targeted by cybercriminals, showing any organization can be at risk.
Cyber security threats have been around for years, and as technology advances, so do the capabilities of cyberattacks. The kind of harm cybercriminals can do to an organization can be very severe, so proper protection from such threats is essential. The first step to establishing the right cyber security systems is knowing what threats exist.
For some of the latest cyber security threats in 2022, keep reading.
What Are Cyber Security Threats?
A cyber security threat is an attack on an IT system that can cause harm. Some common reasons for a cyber-attack include:
- Stealing data
- Damaging data
- Causing disruption
- Controlling a network
There are various ways to improve IT security to protect from cyberattacks. As forms of protection improve, so do the techniques used by cyber attackers. This means that a business needs to stay up to date with cyber security trends to maintain the best protection.
Cyber Security Threats in 2022
There is a wide range of types of cyberattacks, and new ones are always appearing. Developers act fast to keep up with cybercriminals to minimize the impact of new types of attacks.
Being aware of the top threats is the first step in keeping your organization as safe as possible.
Supply Chain Attacks
Supply chain attacks started to become a lot more common towards the end of 2021, and they have continued to rise since then. The SolarWinds hack played a large part in this.
Using backdoor code, hackers managed to compromise the SolarWinds development environment. They were then able to monitor it through its Orion network using the Sunburst malware.
Various forms of this malware were being used to attack a range of organizations, leading to a huge number of supply chain attacks throughout 2021 and into 2022. Of these, the most famous is the Log4j zero-day vulnerability. These attacks haven’t slowed, and are likely to grow throughout 2022.
Cyber Pandemic
The Covid-19 pandemic had a huge impact on the way many businesses work. Most office-based employees moved from working in-office to working from home, and this is likely to continue because it has presented several benefits.
To make this work, many businesses had to implement new systems that allowed people to work from remote locations. One result of this is that the first line of defense for many organizations became the personal devices of their employees.
With businesses operating in this way, a range of new vulnerabilities have come into play. Many companies seem to want to move forward with staff working remotely, so it’s more than likely that hackers will continue to take advantage of this new way of working.
Cloud Service Targeting
One significant change as a result of increased remote working is the adoption of cloud computing. Almost all organizations that have had people working from home have increased their cloud computing systems, and for some companies, this is their first use of the technology.
Employees often need to access applications and data from a business’s network, and cloud computing makes it easy. This increased use of cloud computing has led to an increase in security measures for such systems, but some vulnerabilities still exist.
There are quite a few vulnerabilities within the cloud infrastructure itself, and by exploiting these, a hacker can attack multiple business IT systems at once. As a cloud network can extend to all systems within an organization, the business impact of an attack like this can be quite significant.
Despite these exploits, cloud computing provides a range of solutions that make it much easier for businesses to function in today’s world. Moving into the future, the use of cloud computing will grow, and the number of attacks will likely grow in kind.
Ransomware
Ransomware has been on the rise in recent years, and it’s potentially a very costly threat for businesses. It typically involves gaining access to a network and holding files for ransom. The attacker will then demand payment before releasing the files back to the victim.
This type of attack can even go beyond disrupting IT systems. In 2021, the Dark Side ransomware group hacked The Colonial Pipeline. In doing so, they shut down a major pipeline along the US East Coast. There have been plenty of similar attacks that have caused various business disruptions.
Attackers have been known to launch ransomware attacks on a range of organizations such as plants, slaughterhouses, and even the education and healthcare sectors.
The best way to protect against ransomware is to ensure all important files and data are backed up. If an attacker accesses your system, you won’t need to pay the ransom if you have a backup copy of everything ready to go.
Mobile Risks
Many organizations are adopting BYOD (bring your own device) policies so that their employees can work from their own devices rather than one supplied by the company. This allows workers to use a device that suits them and saves on business expenses.
One downside to this, however, is that it reduces security visibility, as devices can’t be monitored in the same way. It also means that organizations can’t respond to threats in the same way as they would with their own devices.
Zero-click exploits allow hackers to take control of people’s devices from which they can access vital data from sources such as email, phone, and text. In recent years, hackers have developed more mobile-based malware Trojans which can take advantage of the lack of security present on most mobile devices.
Cyber security software for mobile devices isn’t as advanced as it is for computers, and many people don’t use any at all. This puts them at a higher risk of attack from cybercriminals.
Social Engineering
Social engineering is somewhat different from most other cyber security threats. Rather than taking advantage of technical vulnerabilities, this makes use of human error. High-quality security systems aren’t easy to breach, meaning this can often be a far more effective technique.
Most data breaches involve some degree of human interaction as hackers know it’s typically easier for them to get in. Phishing and email impersonations are common examples of this – relying on someone to unwittingly click a malicious link in an email, allowing a hacker to launch their attack.
Similar methods have become very common in the cryptocurrency space. By getting someone to click on a link, a hacker may be able to completely drain the wallet of their victim. With the increased adoption of Bitcoin and other cryptocurrencies, this is only likely to increase.
Third-Party Exposure
If a certain network is connected to other, less-protected networks, a hacker may be able to use these third-party networks to get around the security measures of their target.
A famous example of this is an attack in 2021 that went through Socialarks. Socialarks was contracted by Facebook, Instagram, and Linkedin, and therefore had access to their networks. This led to data from over 214 million accounts from these three platforms being leaked.
A small business trying to expand might make use of third-party contractors and freelance workers. In doing so, they may be more exposed to these kinds of threats.
Internet of Things
Many homes and businesses now have one or more IoT devices set up. IoT devices consist of things like:
- Smart doorbells
- Smart thermostats
- Personal digital assistants (Alexa, Siri, etc.)
These devices make people’s lives more convenient, but many people don’t realize the security risk they pose. IoT devices typically have little to no security measures, so hackers may be able to access home or business networks through them.
Smart devices are only growing in popularity, meaning the number of attacks will also increase. The more smart devices that are connected to a network, the more potential ways there are for a hacker to launch an attack.
How to Protect Yourself From Cyber Security Threats
With the range of cyber security threats in today’s world, it can be almost impossible to protect yourself from them all. There’s a range of developers with different cyber security software available. These generally offer some good protection and act as a threat deterrent, but are far from offering full coverage.
One thing you should do is ensure your employees are aware of the cyber security threats they may be exposed to. If they know what types of attacks to watch out for, they’ll have a much easier time avoiding them.
For the best protection, you should consider a managed IT service. Securelogic Solutions offers a range of IT support services to assist businesses in a range of ways. Our cyber security services will help protect your network and keep your data secure.
Protecting Your Network
With the assistance of Securelogic Solutions, you can greatly reduce the risk that cyber security threats pose to your network. We’ll ensure all security is up to date and able to protect against the latest threats. We also provide several other services such as cloud hosting, endpoint management, and network monitoring.
Click here to speak to Securelogic for more information or to assess your cyber security risk and posture. The team is always happy to help.